HashiCorp Vault Enterprise PKI (v1.10–v1.14+)
Prepared by SafeCipher — vendor‑neutral PKI & cryptography consultancy. This deep dive blends product facts with SafeCipher’s field guidance so you can choose the right CA approach for regulated, hybrid, and multi‑cloud estates.
What is HashiCorp Vault PKI? (Private CA, MTLS, Certificate Automation)
HashiCorp Vault Enterprise includes a PKI secrets engine that issues and manages X.509 certificates for internal TLS/MTLS. It provides API‑driven issuance, role policies, CRL/OCSP revocation, short‑lived certs, and tight integrations for Kubernetes, service meshes, and traditional workloads.
What’s New in Vault PKI v1.10–v1.14+ (Managed Keys, Multi‑Issuer Rotation, Unified CRL, ACME)
- v1.10 – Managed Keys for PKI: Store and use CA private keys in HSM (PKCS#11) or cloud KMS (AWS KMS, Azure Key Vault) without exporting keys.
- v1.11 – Multi‑Issuer & Cross‑Signing: Multiple issuers per PKI mount enable in‑place key rotation, staged rollovers, and cross‑signs.
- v1.13 – Unified Revocation: Unified CRL across clusters, improved OCSP publishing, and tidy jobs for long‑lived artefacts.
- v1.14+ – Built‑in ACME Server: Native ACME for automated issuance/renewal with cert‑manager, Certbot, and web proxies.
- Enterprise – Device/IoT Enrollment: EST, SCEP, CMPv2 endpoints for MDM/EMM, Windows/macOS, and embedded/IoT fleets.
Vault PKI Architecture (Offline Root CA, Online Intermediate CAs)
- Hierarchy: Offline Root CA (HSM) + online Intermediates in Vault; optional cross‑signing for trust continuity.
- Namespaces & Multi‑Tenancy: Per‑team or per‑tenant isolation with delegated admin and policy boundaries.
- Performance/DR Replication: Regionally distributed PKI mounts, per‑cluster AIA/OCSP/ACME URLs.
- Policy as Code: Sentinel/OPA‑style controls; enforce subject/SAN patterns, key usages, TTLs, and path length.
HSM / KMS Key Protection for CA Keys (PKCS#11, AWS KMS, Azure Key Vault, BYOK)
- Managed Keys keep CA private keys in FIPS‑validated HSMs or cloud KMS with dual control & audit trails.
- Support for PKCS#11 HSMs, AWS KMS, Azure Key Vault (Managed HSM), and BYOK/attestation patterns.
- SafeCipher note: Treat Managed Keys like classic HSM ops—formal key ceremonies, split knowledge, escrow policies, and immutable audit.
Certificate Automation with ACME, cert‑manager, and Kubernetes (Ingress, Service Mesh, MTLS)
- Built‑in ACME server enables 60–90 day short‑lived certificates and hands‑free renewals.
- Works with cert‑manager Issuer/ClusterIssuer, NGINX/Envoy/Traefik ingress, and Istio/Linkerd service meshes.
- SafeCipher note: Use short TTLs for servers; for devices, justify longer lifetimes with rotation windows and revocation reachability.
Device & IoT Enrollment (EST, SCEP, CMPv2) for MDM/EMM and Embedded Fleets
- Enterprise endpoints for EST, SCEP, and CMPv2 integrate with Microsoft Intune, Jamf, MobileIron, and IoT bootstrapping flows.
- Ideal for 802.1X, EAP‑TLS, VPN client certificates, secure manufacturing onboarding, and brownfield OT/IIoT.
- SafeCipher note: Align enrollment with asset inventory and SBOM sources; enforce proof‑of‑possession and per‑tenant namespaces.
Revocation at Scale (CRL, OCSP, Unified CRL, Delta CRL)
- Publish CRL (full/delta) and OCSP responders per cluster; align AIA/OCSP URLs with replication topology.
- Unified CRL simplifies distribution across HA/performance clusters; schedule tidy jobs to control storage growth.
- SafeCipher note: Design for revocation reachability first—proxies, caching, and appropriate CRL sizes—then tune issuance rates.
Security & Governance (RBAC, OIDC/LDAP, FIPS Builds, Audit Logging)
- Auth methods: OIDC, LDAP, Kubernetes, AppRole, cloud IAM.
- FIPS builds and detailed audit logging support regulated industries (finance, healthcare, public sector).
- Quotas/rate‑limits per role; namespacing prevents policy bleed‑through.
- SafeCipher note: Enforce SAN/subject patterns and EKUs with policy; block wildcards unless explicitly approved.
Vault PKI vs EJBCA vs Venafi vs AWS Private CA vs Google Cloud CAS vs Smallstep (Feature Comparison)
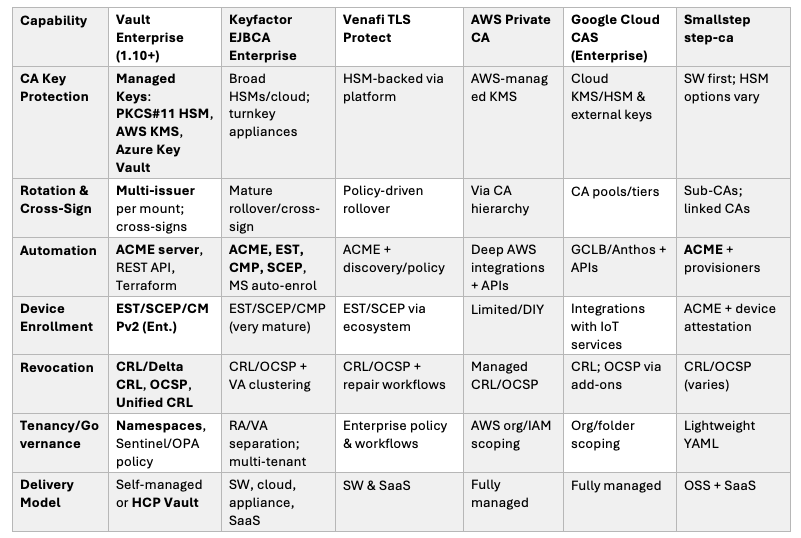
SafeCipher takeaway: Choose Vault for programmable PKI inside your secrets platform with HSM/KMS and ACME/Kubernetes automation. Choose EJBCA/Venafi for advanced RA/VA workflows at massive scale. Choose AWS PCA/Google CAS for cloud‑native managed integrations. Smallstep is a lean ACME‑first option.
When to Choose HashiCorp Vault PKI vs Alternatives (Use Cases & Decision Guide)
- Choose Vault Enterprise PKI if you already run Vault, need API‑first PKI, and want HSM/KMS‑backed CA keys with ACME for Kubernetes and web workloads.
- Choose EJBCA or Venafi if you require mature EST/SCEP/CMP, RA/VA separation, inventory/workflows, and compliance reporting.
- Choose AWS Private CA or Google CAS for fully managed cloud CA tightly integrated with load balancers, service meshes, and IAM.
- Hybrid is common: Vault for app/service MTLS; specialist PKI or cloud CA for device onboarding and perimeter.
Reference Architectures (Offline Root, Hybrid RA, Cloud‑Anchored PKI)
- Offline Root + Online Intermediates in Vault (HSM/KMS)
- Root in HSM offline; Intermediates in Vault with Managed Keys. Multi‑issuer rotation; ACME for apps/ingress; Unified CRL + OCSP.
- Hybrid: Vault as Issuing CA behind EJBCA/Venafi RA
- Keep enterprise RA/policy; use Vault for issuance to cloud‑native namespaces and Kubernetes clusters.
- Cloud‑Anchored PKI with AWS PCA / Google CAS
- Use managed CA for L7 integrations; bridge/chain to Vault for internal MTLS and developer platforms.
Operational Best Practices (Tidy Jobs, AIA/OCSP URLs, Rotation, Compliance)
- Tidy: schedule tidy for certs/keys and ACME artefacts (accounts, orders, authz).
- Cluster URLs: configure AIA/OCSP/ACME per cluster/perf node; validate from client networks.
- Rotation: use multi‑issuer to stage new keys; maintain cross‑signs; audit trust stores.
- Compliance: document key ceremonies; enable FIPS builds; centralise audit logs; apply quotas/rate limits.
- SafeCipher note: Maintain a golden set of trust stores and automate propagation to proxies, workloads, and device fleets.
SafeCipher Viewpoint (Vendor‑Neutral)
If you already depend on Vault as your control plane for secrets and identity, use Vault for PKI to minimise moving parts and maximise automation. For enterprises with complex device onboarding (MDM/EMM, EST/SCEP/CMPv2 at scale) or strict RA/VA separation and compliance workflows, EJBCA or Venafi are usually a better primary. For workloads anchored to a single cloud with managed integrations, AWS PCA or Google CAS reduce operational overhead. Most clients adopt a hybrid: Vault for app/service certificates, plus a specialist PKI or cloud CA for devices and perimeter.
Next Steps: SafeCipher Engagement Plan
- Discovery: Map current trust stores, issuance flows, and revocation paths (CRL/OCSP reachability).
- Design: Decide Vault‑centric, alternate, or hybrid model; define namespaces, roles, and governance.
- Pilot: Stand up a Vault PKI sandbox with Managed Keys, ACME, Unified CRL/OCSP; integrate one Kubernetes cluster and one non‑K8s ingress.
Rollover rehearsal: Use multi‑issuer to simulate key rotation and validate client trust continuity
