Prepared by SafeCipher — vendor‑neutral PKI & cryptography consultancy. This guide mixes facts with field‑tested advice to help you choose and deploy EJBCA Enterprise or EJBCA SaaS for regulated, hybrid, and multi‑cloud estates.
What is Keyfactor EJBCA Enterprise/Cloud? (Private CA, RA/VA, Certificate Lifecycle)
EJBCA is a mature, modular PKI platform covering Certification Authority (CA), Registration Authority (RA), and Validation Authority (VA) roles with clustering and high availability options. It supports broad enrollment protocols (ACME, EST, CMP, SCEP, Microsoft Autoenrollment) and rich REST/SOAP APIs, with delivery as self‑managed software/appliance, Enterprise Cloud images, or fully managed EJBCA SaaS.
Why EJBCA for enterprises (Highlights)
- Protocol breadth: Native ACME, EST, CMP, SCEP, Microsoft Autoenrollment for Windows ecosystems and device/IoT fleets.
- Separation of duties: Distinct CA/RA/VA components and External RA with peer connectors for scalable, audited enrollment.
- Ops flexibility: Software, hardware appliances, cloud marketplace builds, or SaaS with SLAs and managed HSM options.
- Multitenancy & scale: Strong tenant segregation and clustering for large hierarchies and high issuance rates.
SafeCipher note: EJBCA is often the quickest route to enterprise‑grade RA/VA separation and device onboarding at scale, while keeping open protocol choices.
Architecture & tenancy (CA/RA/VA, External RA, Peers, Clustering)
- Modular roles: Deploy CA, RA, and VA on separate nodes or clusters. External RA supports polling and hardened DMZ placement.
- Peer connectors: Secure connections between CA and RA/VA tiers simplify multi‑site deployments and network segregation.
- Multitenancy: Run multiple hierarchies and tenants on one cluster with scoped admin and policy controls.
- Cloud & appliance options: Enterprise Cloud AMIs/VM images and EJBCA SaaS (AWS/Azure Marketplace) with managed updates and SLAs.
Protocols & automation (ACME, EST, CMP, SCEP, Microsoft Autoenrollment)
- ACME: First‑class ACME server compatible with popular clients (cert‑manager, Certbot, acme.sh, acme4j) for web, API gateways, and Kubernetes ingress.
- EST: RFC 7030 for device enrollment and renewal with proof‑of‑possession.
- CMP / CMP for 3GPP: Telecom‑grade flows and key update/renewal semantics.
- SCEP: Legacy network device enrollment at scale.
- Microsoft Autoenrollment: Integration for AD‑joined endpoints and NDES‑based scenarios.
SafeCipher note: Use EST or CMP for security‑sensitive device fleets; keep SCEP for brownfield only with compensating controls.
HSM/KMS and key protection (PKCS#11 HSMs, CloudHSM, Azure Key Vault options)
- Broad PKCS#11 HSM support on‑prem and in cloud (e.g., AWS CloudHSM, Azure Managed HSM/Key Vault‑backed keys in SaaS options).
- Support for offline Root CA ceremonies, online Intermediate CAs, cross‑signing and staged rollover.
- Audit trails, dual control, and tamper‑evident logging aligned to compliance frameworks.
Revocation & validation (CRL, Delta CRL, OCSP, VA clustering)
- Publish CRL/Delta CRL and operate OCSP via dedicated VA components; scale VA independently from issuing CAs.
- Tuning for CRL partitioning and caching; options for geographically distributed responders.
EJBCA delivery models (Enterprise, Enterprise Cloud, SaaS)
- Self‑managed software/appliance: Full control, integrates with existing HSMs and SIEM.
- Enterprise Cloud: Pre‑built images/automation in public clouds.
- EJBCA SaaS: Managed service with SLAs, rapid provisioning, and cloud‑native elasticity; marketplace subscriptions on AWS and Azure with managed HSM‑backed keys.
SafeCipher note: SaaS accelerates time‑to‑value for greenfield PKI or as a scalable RA/VA layer in front of an existing CA.
Integration patterns (Kubernetes, MDM/EMM, IoT/OT, Telecom)
- Kubernetes: Use ACME with cert‑manager (Issuer/ClusterIssuer) to automate ingress and internal MTLS.
- MDM/EMM: Integrate with Intune, Jamf, and NDES/NDES‑alike for device certs (802.1X/EAP‑TLS, VPN).
- IoT/OT: EST/CMP workflows for manufacturing bootstrap, secure provisioning, and long‑lived device identity.
- Telecom: CMP/3GPP support for 4G/5G elements.
Reference designs we deploy (SafeCipher)
- Offline Root + EJBCA Enterprise Intermediates (HSM)
- Root in offline HSM; issuing Intermediates clustered. RA/VA tier split; ACME for apps; EST/CMP for devices; OCSP via VA cluster.
- EJBCA SaaS RA/VA + On‑prem Issuing CA
- Use SaaS for enrollment and validation at the edge; peer back to an internal issuing CA to retain key custody.
- Cloud‑native PKI
- EJBCA SaaS in AWS/Azure with CloudHSM/Key Vault; integrate cert‑manager and cloud load balancers; publish CRL/OCSP via CDN.
Operational guidance (policies, rollover, audits)
- Profiles & roles: Lock down subject/SAN patterns, EKUs, key sizes/algorithms (P‑256/Ed25519/2048+), and TTLs.
- Rollover: Stage new keys with cross‑signs; test trust stores; gradually flip AIA/OCSP URLs.
- RA hardening: Place External RA in a DMZ with mTLS to CA; rate‑limit enrollments; enable proof‑of‑possession.
- Monitoring: Stream RA/CA/VA logs to SIEM; alert on issuance spikes, OCSP latency, and CRL size growth.
Pros & cons (Quick view)
Pros – Deepest protocol coverage (ACME/EST/CMP/SCEP + MS Autoenrollment) and RA/VA separation. – Flexible delivery (software, cloud, SaaS) and broad HSM/KMS choices. – Telecom and device/IoT at scale; strong multitenancy.
Cons – More moving parts (RA/VA/clusters) than cloud‑native managed CAs. – Requires PKI expertise for policy design and life‑cycle governance. – For app‑only, API‑first use cases already on Vault, Vault PKI may be simpler operationally.
EJBCA vs HashiCorp Vault vs Venafi vs AWS Private CA vs Google CAS vs Smallstep (Feature Comparison)
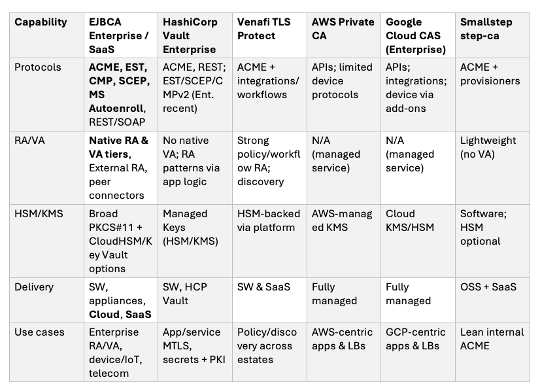
SafeCipher takeaway: Choose EJBCA when you need protocol breadth and turnkey RA/VA at scale. Choose Vault for API‑first PKI inside an existing Vault control plane. Choose Venafi for enterprise discovery/policy orchestration. Prefer AWS PCA/Google CAS when managed, cloud‑native integration outweighs custom control. Smallstep excels as a lean ACME‑centric CA.
When to choose EJBCA vs alternatives (Decision guide)
- Choose EJBCA for device/MDM/IoT onboarding (EST/CMP/SCEP), RA/VA separation, telecom, and multi‑tenant PKI.
- Choose Vault for developer‑led automation tied to secrets/identity and ACME for apps.
- Choose Venafi if estate‑wide discovery, workflows, and policy enforcement are primary.
- Choose AWS PCA / Google CAS when you want fully managed CAs tightly integrated with cloud L7 and IAM.
- Hybrid is common: EJBCA for device/RA; Vault for app certs; cloud CA for LB/service‑mesh.
Next steps with SafeCipher
- Discovery: Map issuance, enrollment protocols, and revocation reachability; review compliance mandates.
- Design: Choose Enterprise vs EJBCA SaaS, HSM/KMS model, RA/VA topology, and profiles.
- Pilot: Stand up External RA + VA, enable ACME/EST/CMP, integrate cert‑manager and one MDM.
- Operationalise: Rollover rehearsal, tidy schedules, monitoring, and playbooks.
