PKI and the Quantum Threat Timeline
You Must have Cryptographic Agility
Important considerations for Quantum Awareness in 2025 and beyond
The above image, outlines four key points, regarding the preparation for post-quantum cryptography, as well as a timeline for transitioning to quantum-resistant algorithms. The points are further summarized below :
Chief Information Officers Awareness and Understanding of the Threat
Chief Information Officers (CIOs) within organizations are encouraged to review cryptographic procurements and data security standards that may need updating to address the emerging post-quantum threat. This point emphasizes the importance of awareness at the senior management level about the potential risks posed by quantum computing to current encryption standards.
the deprecation of RSA-2048 & ECC-256 by 2030
NIST is leading the global shift toward post-quantum cryptography, targeting the deprecation of RSA-2048 and ECC-256 by 2030 and their complete phase-out by 2035. This initiative addresses the growing threat posed by quantum computers, which could render classical encryption obsolete and expose sensitive data to breaches through “harvest now, decrypt later” tactics.
Organizations must act decisively—conducting cryptographic inventories, assessing exposure, and migrating to quantum-resistant algorithms to safeguard data with long-term confidentiality needs. Collaborative actions, including the adoption of shorter certificate lifecycles, hybrid cryptographic models, and cloud-native PKI architectures, will be essential for both public and private infrastructures to achieve quantum resilience efficiently.
Identify What Data May be at Risk
It’s crucial to determine which data could be compromised once a quantum computer becomes available. The graphic mentions the possibility of a “hack now, decrypt later” attack, where adversaries collect encrypted data today with the intention of decrypting it once quantum computing becomes sufficiently advanced. This underscores the need for proactive risk assessment of sensitive data.
Organizations Should Already be Planning a Migration Plan
Organizations are advised to start planning for the transition to post-quantum cryptography in response to the NIST (National Institute of Standards and Technology) post-quantum algorithm standardization. The process should include creating migration plans for legacy cryptography, which is especially vital for cryptography that is not agile or easily updated.
PKI is Especially Vulnerable to a quantum attack
Public Key Infrastructure (PKI) represents one of the most exposed components in the face of quantum computing threats. Its reliance on RSA and ECC makes it highly susceptible to future quantum decryption capabilities, putting root trust anchors, certificate hierarchies, and digital identities at risk.
Given PKI’s long operational lifespan, organizations should establish a quantum readiness roadmap now—prioritizing cryptographic inventories, algorithm agility, and phased adoption of quantum-resistant primitives. A proactive transition plan will be critical to preserving trust across distributed, regulated, and high-assurance environments once quantum-safe standards are fully ratified.
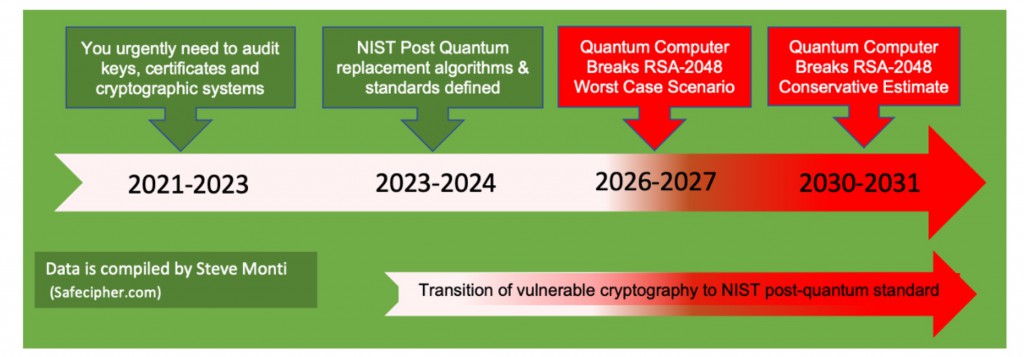
Timeline for a quantum Transition
The timeline arrows in the above diagram, indicate an urgent need to audit keys, certificates, and cryptographic systems between 2021-2023. By 2022-2025 (now), NIST post-quantum replacement algorithms and standards are already partly defined. Safecipher and other companies, are already building PKI with NIST approved algorithms. Between 2026-2027, quantum computers may be able to break RSA-2048 encryption, which is described as a worst-case scenario. A conservative estimate places this risk between 2030-2031.
